Cloud Sovereignty explained
Cloud Sovereignty is both a growing concern and interest from customers as well as a term that's increasingly a buzzword. In fact, it's becoming difficult not to come across an established cloud solution provider or a digital infrastructure management solutions provider who won't dabble into cloud, digital or data sovereignty one way or another.
At Vates we have been developing virtualization and infrastructure management solutions for over 10 years in Grenoble, in the French Alps. This means that we as a company are subject to French laws and European Union's regulations. In other words, this makes us a software vendor that does not have to comply with current extraterritorial laws from non European Union member states, other than the now world famous GDPR on personal data protection. But perhaps more importantly our mission is to provide our customers with the right tools to run their IT infrastructure and to enable them to be completely free and independent - no strings attached.
The question that may come up at this point is how all of the above intersects with sovereignty and cloud sovereignty. Let's start in a simple way: cloud sovereignty can be defined as the ability to own, operate and master a digital infrastructure, be it a datacenter, a set of distributed hardware servers and equipment, a full blown private cloud or a combination of each of these.

These three combined abilities, ownership, operations and mastering, when fully understood and put into the proper context, lay the right foundations for cloud sovereignty. It is at this point important to remember that sovereignty is a concept that fundamentally applies to a state. In the classic theory of state sovereignty there are a number of clear attributes that make a state truly sovereign. Here we will just work with the notion that sovereign clouds exist and run within defined geographical locations and these locations indicate in turn what national law applies.
What we now have is an approach that combine several layers that help show whether a cloud may be deemed to be "sovereign" or not:
- geographical location of the infrastructure(s)
- nationality of the software stack(s) used to power the cloud infrastructure
- nationality and applicable law of the data processed in the infrastructure
- nationality of the cloud infrastructure owner or operator.
- nationality of third party supplies (physical security at the infrastructure physical location, hardware manufacturer, etc.)
- ability of the cloud infrastructure operator to effectively take over the maintenance and development of the software stack (both at the infrastructure and perhaps at the application level) used in the cloud
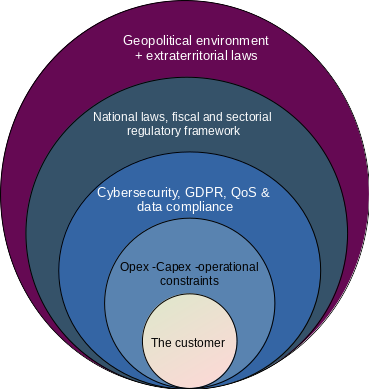
All these elements highlight a complexity in our ability to assess whether a cloud may be rightly called sovereign. To some extent this might even be seen as a spectrum. Where the crux of the issue lies is for customers to know whether:
- they can freely either take over , replace or avoid vendor lock-in with the cloud infrastructure
- they are directly or indirectly subjected to extraterritorial regulation of measures because the cloud operator introduces a liability on a foreign extraterritorial law
- they comply with their own industry-wide and of course national regulations.

Of course, just to add even more confusion, some extraterritorial regulations essentially work through and in spite of cloud operators or even software vendors: the very fact of relying on a software that has been developed in one specific country creates a liability for its user as she may be spied on and its data transferred over to another part of the world for the nebulous reason (pun intended) of "national security purposes". Therefore One should judge a cloud or digital infrastructure solution not on its claims but on all the above criteria mentioned above.
While it may not be in the power of Vates to give its customers the ability to meet all their regulatory compliance criteria, we can at least help in two critical areas.
1) We are and always will be Open Source
Our code is publicly developed, published and documented. We are one of the major contributors to the Xen Project hosted by the Linux Foundation and there again, everything is documented. There are no strings attached. Of course, we want our users to understand that we depend on them to further our work and our growth by ensuring their infrastructure is properly supported - but we give you the keys to our software and there's no vendor lock-in. You could even fork it if you wish to.
2) The sole extraterritorial regulation we have to comply with is GDPR
No National Security letters. We provide software that you may freely use, run, study, modify, operate in the location of your choosing on an infrastructure you own and that you can master. We put no backdoors in it. And you're welcome to audit it, all the more so as our code is open. Did we forget mention it? We're open source.
As always we are happy to hear from you, your projects and your feedback .



